With some friends at kernelmode.info, we have made a sort of 'monitoring team' for investigate this ransomware family. (i've profited of this to stop publishing unlock code for this one on my blog)
I will not tell what's we do and how we proceed but it's relatively easy to get the newest fake porn sites (even inactive domains who will be used in near future) by these bad guys.
The 'WinAD' gang are known for these winlocks:
'Bluetrash'
'Homoblocker'
'Pornorolik':
They are also known for using crypters such as Mystic compressor and VBCrypt.
The web process for get infected work like this
1) Fake porn site send you to the 'redirector'
2) The redirector send you to another fake porn site
3) The fake porn site conduct to malware download:
Note: new domains are spawn daily and same for the redirector who get all his links updated.
It's daily reversing for get unlock code of the day.
--
The first machine is a Sutra TDS (Traffic Distribution System)
The redirector if you prefer
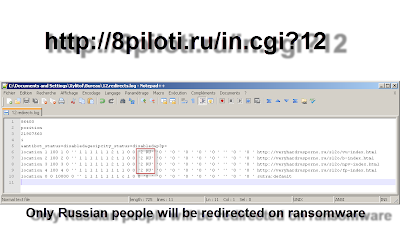
Curently every redirector url used by these guys are named "in.cgi" (a elf file) who searh the good log file in function of the parameter passed.
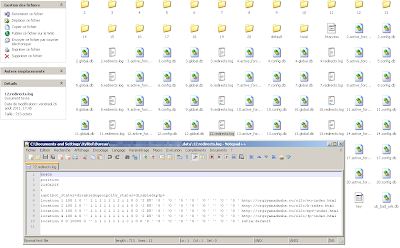
Structure of the TDS:
The folder /data/ who have an htacess "deny from all" is used for redirect users.
The parameter '12' will send you to ransomware fake porn site:
Some factice sites are also here, in case if you don't come from Russia and with some others parameters:
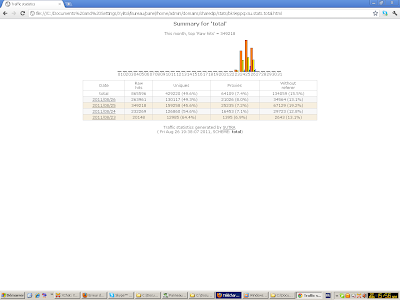
SQLitle db dump, here the referers:
Pornorolik domains tracked (and this just for 25-26 Aug):
Stats (TDS dumped the 26)
That all for the TDS machine.
Now the fake porn site who conduct to malware download
Fake pages who conduct to malware download are in html (lol) a javascript code is used for display thumbles and the folder video just contain 'videos12.avi.exe'.
The folder diz-videoyou contain the site design and some php related to advisories
Folder 'diz-bravo' is also advisories related
diz-freshporn contain another website kit template
diz-npv contain 'new porno video' image for another kit.
As you can see nothing is 'developped' on these servers, pages are primitive.
The porn business seem good enought to infect people.
Bad guys who are under this use probably another machine (a windows?) with a timer who each x time rebuild/repack the ransomware and upload it automaticaly to servers, and can do a RDP connect for see what's going on. (that just my opignon about how they work, if you know more about these guys don't hesitate to contact me)
They bought also new domains each day and refresh their beeline numbers.
For do that... sure they have money.
WinAD related:
Bluetrash ransomware.. now updated with a bot.
Trojan.Ransom (HomoBlocker)
Trojan.Ransom (porn2o-rolik2.avi.exe)
(ext) Trojan Ransom (WinLock), a growing threat
Edit: Thanks to kmd for the picture :þ






















I have heard about the WinAD guys. It is a sad thing how the internet is being exploited these days. I write a lot about the Cyber Crime and Computer Awareness to alert the people. Oh well, something that I can do from my part.
ReplyDelete